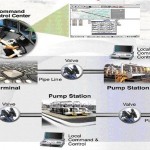
The real-time data on the multi-lingual HMI screen in control room gives the operator an ability to monitor the situation of the pipeline. Moving the mouse pointer on the relevant area on the main screen will create a thin border around the area described by the secondary screen. Clicking on any point inside the border will cause this secondary screen to appear. Clicking on the valve name at the main screen subtable will pop up the relevant valve subscreen, and the operator will be able to operate the valve. All customization required for the different pipeline applications is performed in software.
The real-time data on the multi-lingual HMI screen in control room gives the operator an ability to monitor the situation of the pipeline. Moving the mouse pointer on the relevant area on the main screen will create a thin border around the area described by the secondary screen. Clicking on any point inside the border will cause this secondary screen to appear. Clicking on the valve name at the main screen subtable will pop up the relevant valve subscreen, and the operator will be able to operate the valve. All customization required for the different pipeline applications is performed in software.
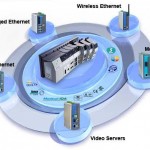
 Over the past decade, critical control systems have increasingly adopted information technologies such as Windows® EthernetTM, TCP/IP and web services. Unfortunately this means that PLC, DCS and SCADA systems are now exposed to attack from viruses, hackers and possibly terrorists from around the world.
Over the past decade, critical control systems have increasingly adopted information technologies such as Windows® EthernetTM, TCP/IP and web services. Unfortunately this means that PLC, DCS and SCADA systems are now exposed to attack from viruses, hackers and possibly terrorists from around the world.
The TofinoTM Industrial Security Solution is implemented in Modcon SCADA to offer a layered security solution for industrial systems by deploying the security appliances directly in front of each control device (or group of up to 16 devices) that need protection. These appliances provide protection directly in front of the critical edge device. This allows a “defense-indepth” strategy to be used, so even if a hacker or virus manages to get through the main corporate firewall, they will still be faced with an array of SCADA-focused security devices that need to be breached before any damage can be done to the control system itself.
 Independently of the CMP installation, the TofinoTM Security Appliances will be installed in front of individual control devices or groups of control devices that require protection. Each appliance is designed to have a “zero configuration” installation procedure where the person who installs the appliance only needs to mount it on a DIN rail or controller chassis and connect the power and communication cables. All appliances will remain in invisible pass-through mode until awakened by the CMP, so they can be installed at any time without impacting the operating process.
Independently of the CMP installation, the TofinoTM Security Appliances will be installed in front of individual control devices or groups of control devices that require protection. Each appliance is designed to have a “zero configuration” installation procedure where the person who installs the appliance only needs to mount it on a DIN rail or controller chassis and connect the power and communication cables. All appliances will remain in invisible pass-through mode until awakened by the CMP, so they can be installed at any time without impacting the operating process.
Appliances can also be installed after a CMP is already commissioned, in which case they will become activated as soon as CMP-to-appliance communications are secured through the automatic Encryption Tunnel/Digital Certificates process.